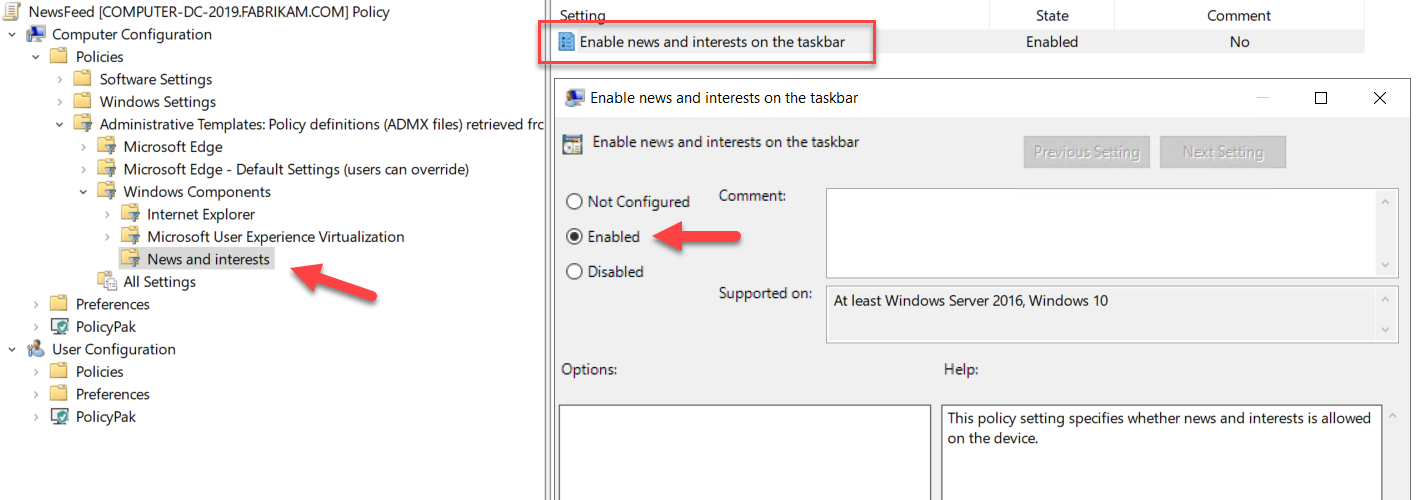
This isn’t my story: This is me sharing THEIR story. In this story, I (Jeremy) am only the narrator. ?
While at a conference, I met two new friends (who already knew one of my friends). A bunch of awesome Danish gents who said to me.. “Hey Mr. Group Policy Guru.. maybe you know… we have a problem when Group Policy updates, some of our applications flicker! And our users are going crazy !”
The guys were: Roland Jørgensen (twitter: @mindlessdk) and Jonas Weinreich (twitter: @weinedk) (both at the conference), and Claus Wordenskjold (twitter: @CWordenskjold) (my original friend, who was NOT at the conference.)
Now I had heard of this issue from time to time. But to set the stage, in fact, a little flicker during foreground and GPudpate is perfectly normal.
In fact, there’s an older web article: https://msdn.microsoft.com/en-us/library/ms812018.aspx which tells the tale..
Consider notifying users that their policy is updated periodically so that they recognize the signs of a policy update. When Group Policy is updated, the Windows desktop is refreshed; it flickers briefly and closes open menus. Also, restrictions imposed by Group Policies, such as those that limit the programs a user can run, might interfere with tasks in progress.
So, if this is expected behavior, why are my Danish pals seeing a more “profound” flicker.. enough to make users call the help desk and start to get pretty annoyed?
You can find others’ with flicker issues if you Goog, I mean.. Bing for it.
- For instance, here’s a resolution with GPupdate flicker + Cortana: https://answers.microsoft.com/en-us/msoffice/forum/msoffice_outlook-mso_win10/the-calendar-in-outlook-2016-is-blinkingflickering/07c3ca0f-4b38-4ad9-857e-f7d486d6e9b1
- Here’s a chat about Group Policy updates making Dynamics flicker: https://community.spiceworks.com/topic/1539867-group-policy-refresh-causing-dynamics-gp-forms-to-flicker-on-windows-10
- Here’s a patch which fixed Outlook To-Do bar flashing with GPupdate: https://www.policypak.com/knowledge-base/general-on-prem-troubleshooting/how-can-i-fix-outlook-to-do-bar-flashing-when-gp-or-policypak-does-a-background-refresh.html
So, yes, I (Jeremy) had heard of it.
I told them I would poke around, and they would too, and we’d meet up. But they found an answer.. and that’s this story.
Problem Statement
So after a little investigation, the team made a problem statement:
- When the computer ran a gpupdate, some applications would flicker.
- Outlook 2016 started flickering, and switching back and forth, going to not responding and blank pages and return to normal.
- Navision 2009 R2 client flickered and the formular which the user was working in would be reset.
- We experienced the issue on both virtual and physical computers, and in a variety of different OS from Windows 8.1 to Windows 10 1607, 1703 and 1709.
- The issue occurs every time a new setting is set a GPO. Thereby it happened every time a policy with a Group Policy Preferences item was run. All of our drive and printer mapping is set in GPO.
To get started to pare it down, they did what I always recommend…
GO NAKED.
By which I mean.. have a computer that is “born fresh”, has all the latest patches, and few applications as possible… JUST FOR TESTING.
This aspect is critical, because you can eliminate SO MUCH from your testing by paring it down and stripping the computer / OS to as basic as you can get.
Then.. BUILD UP you machine.. and find WHEN the problem STARTS.
And.. with this technique, they were able to start with a “pretty naked” machine, as soon as Group Policy applied, and Group Policy Preferences were re-applying, the “mega flicker” issue occurred.
Next step: Event Logs
My Danish friends got different reports and different applications flickering. But for them, it was Outlook that was driving them crazy, and flickering all the time.
So… with Group Policy, the best place to START troubleshooting would be.. the event log ! On the first computer they checked, they saw GPOs being refreshed every minute.
Then, some time later, it started to refresh every 5 seconds!
Crazy!

Log Name: System
Source: Microsoft-Windows-GroupPolicy
Date: 16-05-2018 16:25:39
Event ID: 1502
Task Category: None
Level: Information
Keywords:
User: SYSTEM
Computer: L-TEST-T480S.internal.org
Description:
The Group Policy settings for the computer were processed successfully. New settings from 8 Group Policy objects were detected and applied.
Event Xml:
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-GroupPolicy" Guid="{AEA1B4FA-97D1-45F2-A64C-4D69FFFD92C9}" />
<EventID>1502</EventID>
<Version>0</Version>
<Level>4</Level>
<Task>0</Task>
<Opcode>1</Opcode>
<Keywords>0x8000000000000000</Keywords>
<TimeCreated SystemTime="2018-05-21T01:17:12.416286700Z" />
<EventRecordID>14030</EventRecordID>
<Correlation ActivityID="{14E5F0E1-F113-47CD-B4F2-D7A2A362F1F4}" />
<Execution ProcessID="6120" ThreadID="12080" />
<Channel>System</Channel>
<Computer>L-TEST-T480S.internal.org</Computer>
<Security UserID="S-1-5-18" />
</System>
<EventData>
<Data Name="SupportInfo1">1</Data>
<Data Name="SupportInfo2">4201</Data>
<Data Name="ProcessingMode">0</Data>
<Data Name="ProcessingTimeInMilliseconds">9953</Data>
<Data Name="DCName">\\ADSERVER.internal.org</Data>
<Data Name="NumberOfGroupPolicyObjects">15</Data>
</EventData>
</Event>
The Discovery… It wasn’t Group Policy at all.
So the team started to kill process after process looking for a solution.
And this is where Claus Wordenskjold found the process that made the problem stop.
When killing ccmexec (SCCM) process, the issue stopped.
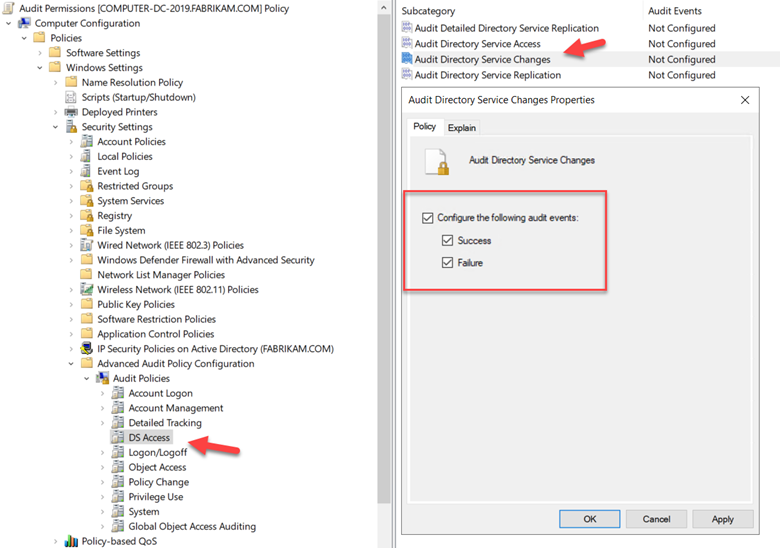
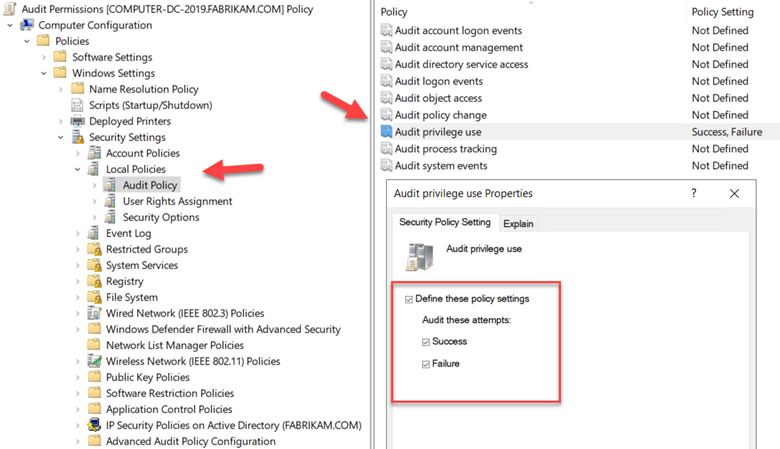
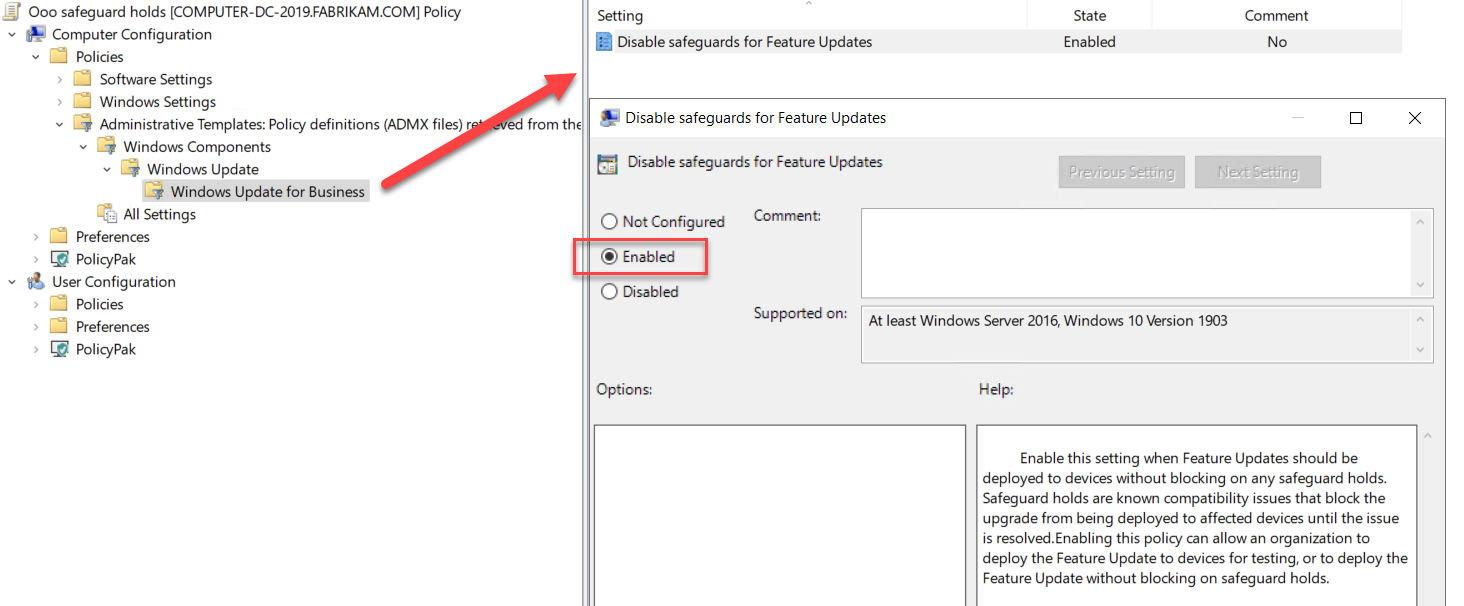
The team proved that it was ccmexec causing the issue, which can be seen in the picture below. You should see four parts.. numbered 1 -4 with four little stories:
- SCCM runs without GPO's applied
- Gpupdate runs every 10th second
- SCCM service is disabled and no GPO’s are applied
- Gpupdate runs as per standard configuration
- SCCM service is disabled and all GPO’s are applied
- Gpupdate runs as per standard configuration
- SCCM service is enabled and all GPO’s are applied
- Gpupdate runs every 10th second
The key thing to look for in each of these stories is the number of 1502 events which expresses the attempt to perform computer-side Group Policy updates. When SCCM was disabled, the 1502 events were normal and not “out of control.”

Event log KEY:
- Event 1500: The Group Policy settings for the computer were processed successfully. There were no changes detected since the last successful processing of Group Policy.
- Event 1501: The Group Policy settings for the user were processed successfully. There were no changes detected since the last successful processing of Group Policy.
- Event 1502: The Group Policy settings for the computer were processed successfully. New settings from X Group Policy objects were detected and applied.
So, in summary: the real issue was not gpupdate or the Group Policy engine. Gpupdate is working exactly as expected.
Solution
So, if killing SCCM processes made Group Policy “happier”, the Danish team needed to dig deeper.
Now, SCCM has a massive amount of logs, so this took a while.
After searching and searching, they discovered a lot of activity in wuahandler.log.
The errors discovered were identical as what is described here:
http://eskonr.com/2014/02/configmgr-onsearchcomplete-failed-to-end-search-job-error-0x80244022-wuahandler-log/
And….
As described in the article, the application pool "WsusPool" in the IIS server on our SCCM distribution point (DP) was stopped. Once it was started it, all of the computers did not refresh every 10th second anymore.
All refreshes returned to normal GPO update behavior.
Conclusion
The programs are still flickering when GPO’s are refreshed, but this is expected and has has always happened.
The problem became obvious and noticeable to end users because GPO refresh happened every 10th second.
People started to notice.
It got weird.
So, why does the failure of an SCCM service make Group Policy “flip out?”
We’re not sure why.
The theory is that the when the SCCM agent cannot see its DP it will try to find a new one. For instance, if a computer moves from one branch office to another, then it might not be able to reach its former DP.
And, the information on where to find the DP is supplied in a GPO targeted the computer.
Thus we think the SCCM agent will trigger it’s own GPupdate, attempting to update only the computer policy. However, we do not have prove of that theory. But that’s what we think is going on.
If you have anything to share, on this interesting case, then just email me (Jeremy) and I’ll compile the best responses and tack them onto the end of the article.
Hope this helps you out.. and happy Group Policy + SCCM co-existence. ?