Enable Auditing for Privilege Escalation with Group Policy
A cyberattack isn’t a sudden single event, but a storyline compromised of multiple stages. First is the initial compromise, followed by the establishment of a foothold or beachhead that the attackers will base operations from. From there the attackers move laterally across the network to perform reconnaissance. The objectives here are to escalate privilege and identify high-value data to target. The final stage is the actual attack itself.
The initial compromise is usually conducted using a compromised standard user account that was captured using a credential stuffing attack or phishing email. To achieve their mission, attackers must work to escalate their privilege to gain access to all areas of the network. This means targeting a privileged user next such as a domain administrator or senior executive. This process may involve the taking over of multiple accounts in the process.
This is why you should enable auditing that will target privilege escalation activities. One option is to enable “Audit Directory Service Changes” which will alert you when a change is made to an AD object. This could be adding a user account to a privilege group for instance or resetting a password. Any alert will provide information about the old and new properties of the changed objects.
To do so, create a GPO and navigate to Computer Configuration > Windows Settings > Security Settings > Advanced Audit Policy Configuration as shown below.
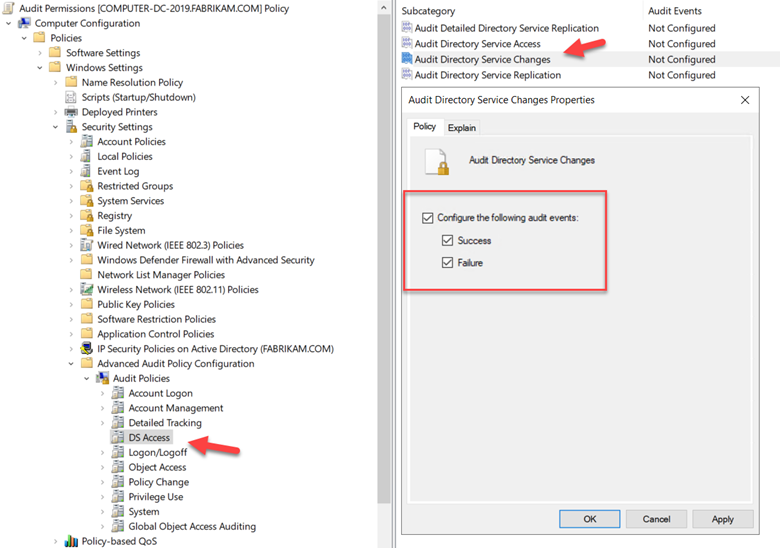
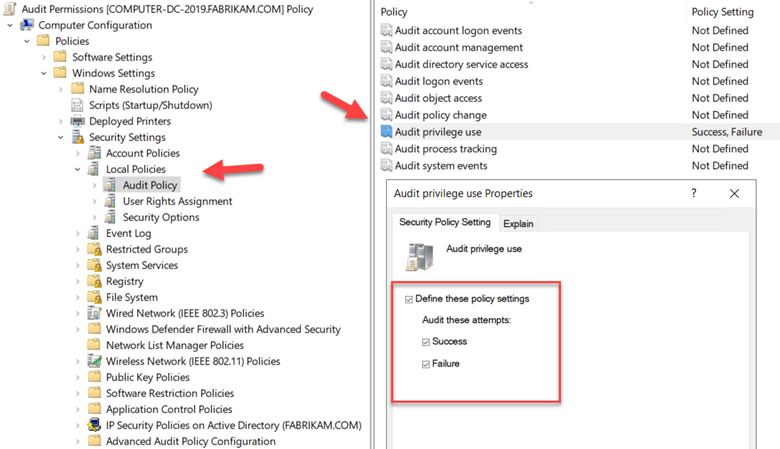
You can also enable auditing for “Privilege Use” which will alert you when a security principle is exercising a user right or privilege. You can do so by creating a GPO and going to Computer Configuration > Windows Settings > Local Policies > Audit Policy as shown in the screenshot below.




Comments (0)