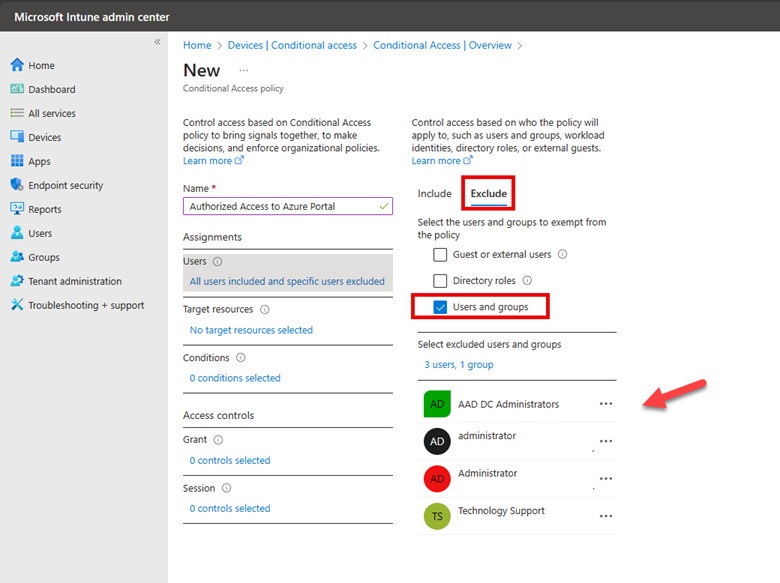
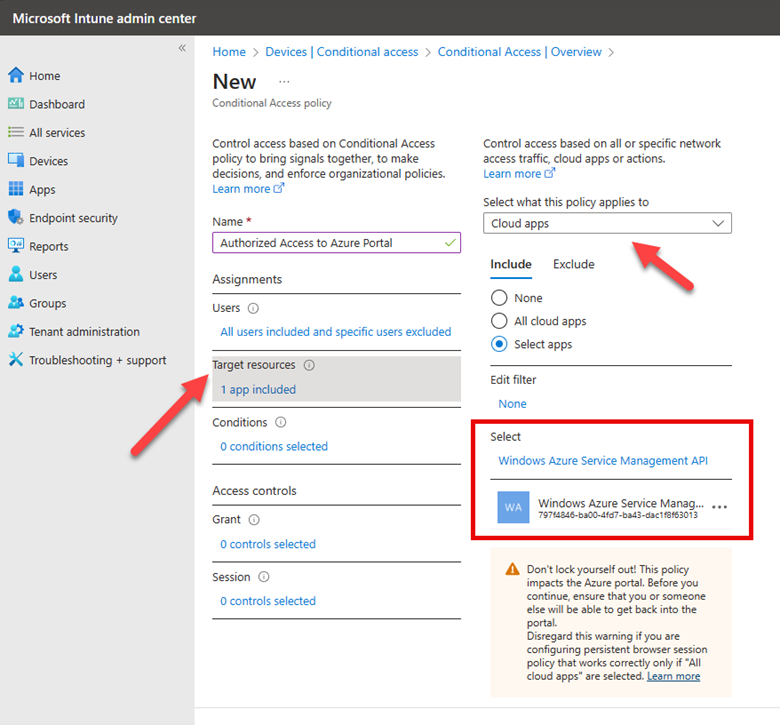
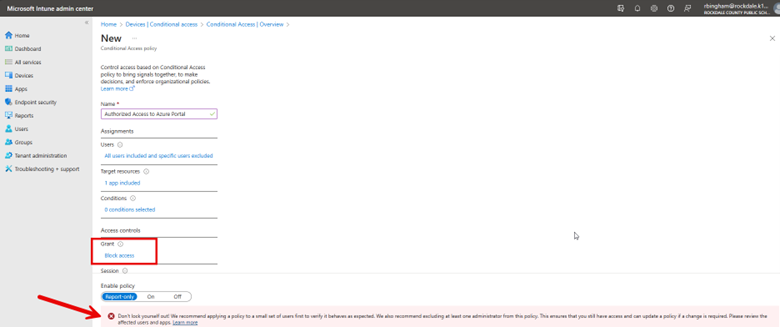
One of the features of Intune is the ability to deploy applications across a wide range of devices and users. For this demonstration I want to install RingCentral for my East Coast Sales users, but first there are some prerequisites to complete first. Using a Windows 11 computer you will need to:
- Download the Microsoft Win32 Content Prep Tool (IntuneWinAppUtil.exe)
- Download the installer for the designated program.
- Create the necessary folder structure for the setup files.
Opting for an MSI file when available is recommended for Intune deployments, as handling EXE files require additional steps and configurations. Once completed, you can begin to wrap the designated application for Intune deployment. Using either PowerShell or a Command Prompt, you will use the series of commands as shown below. In this scenario, the IntuneWinAppUtil is located within a folder named "Intune," containing both a "Source" and an "Output" subfolder for organizing the necessary files.
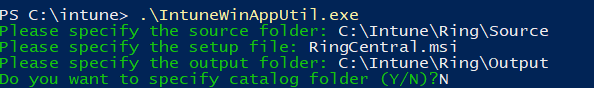
You can also type a single command that will look like this:
IntuneWinAppUtil.exe -c -s -o
In this example, I didn’t need to specify a catalog folder. When required, the Catalog Folder contains any configuration files, scripts, or other resources required by the application during its deployment process. Including this folder ensures that all necessary components are packaged together, facilitating a smoother and more reliable installation process when the application is deployed via Intune to end-user devices.
When you run the command successfully it should look something like the screenshot below.
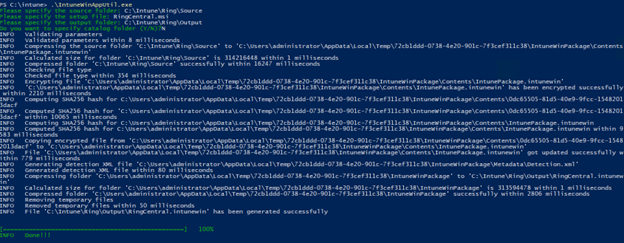
The purpose of the wrapping process is to create the required ‘.intunewin’ file as shown below:
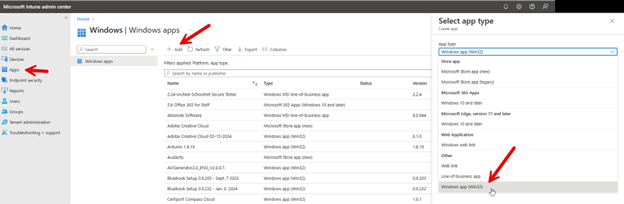
With the wrapping process complete, you are ready to upload the file to Intune. Using the Microsoft Intune Admin Center, navigate to Apps > Windows and click Add and select Windows app (Win32) from the dropdown menu as shown below.
Then you need to upload the application package file that was created using the Content Prep Tool.
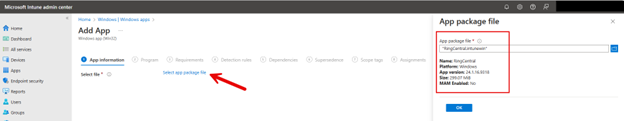
Once I clicked ‘OK’ Intune filled in the required settings under App Information other than Publisher which I provided. In the next screen, Program, Intune then added the install and uninstall commands automatically as shown below.
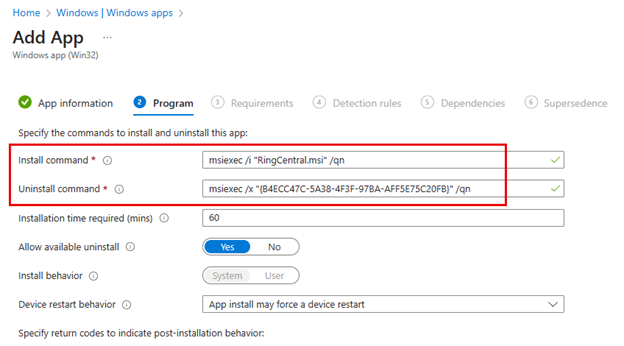
In the Requirements screen you will need to provide the Operating System architecture as well as the minimum operating system required.
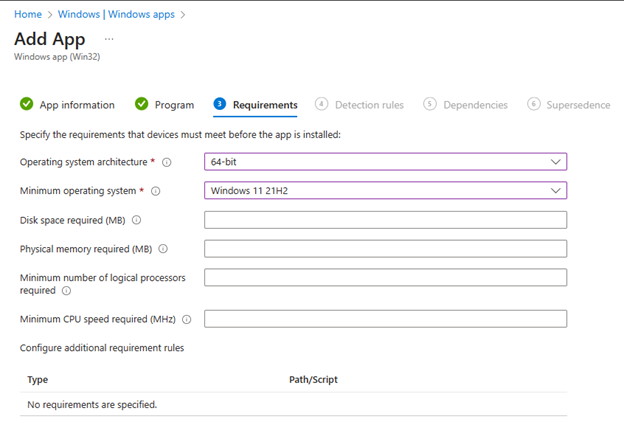
The next screen requires you to create a detection rule for Intune using. You generally define the rule within the Intune application deployment settings to verify if the application is already installed on a device. This involves specifying the path where the application is expected to be installed, and optionally, a file or executable within that path. For example, you might set a rule to check for the presence of an application executable in the "Program Files" directory. If the specified file is found, Intune considers the application installed; if not, it will proceed with the installation. This approach helps prevent reinstallation of applications already present on the device. In the screenshot below I have manually provided the path to the ProgramFiles folder where the RingCentral folder and application resides.
While dependencies and supersendence aren’t necessary here, let’s review what they are. Software dependencies section is for applications that must be installed before this application can be installed. The Supersedence section allows administrators to specify a new version of an application that should replace an older version already installed on devices. By defining supersedence relationships, Intune can automatically update or uninstall the previous version of the app when the new version is deployed, ensuring that users always have access to the latest features and security updates while maintaining a clean and optimized device environment.
Not needing scope tags either, we are ready to move to the final step which was to assign the app deployment policy to the East Sales Users group and then review and create the policy. Once complete, the designated users will receive the application.