How to Validate Dynamic Groups in Microsoft Intune
There are two different types of groups you can create with Intune. The first is the traditional “Assigned Group” in which administrators manually add or remove members. This means of course that group membership only changes when an administrator makes a change. These are best for small organizations or small stable groups within a larger enterprise.
“Dynamic Groups” offer an automated approach to group management, where membership is determined by specific query rules and conditions. Here, members are added or removed in real-time as they meet or no longer meet the specified criteria. These are ideal for large enterprises, large groups that change membership, or large-scale deployments based on departments, locations, or device types.
How to Create a Dynamic Group
There are two ways to create dynamic groups. The first is using the Microsoft Intune admin center and navigating to Groups and select “New group.” On the next page you will create a name for the Group and state whether it is an Assigned or Dynamic group. In the screenshot below, I have selected Dynamic Device.
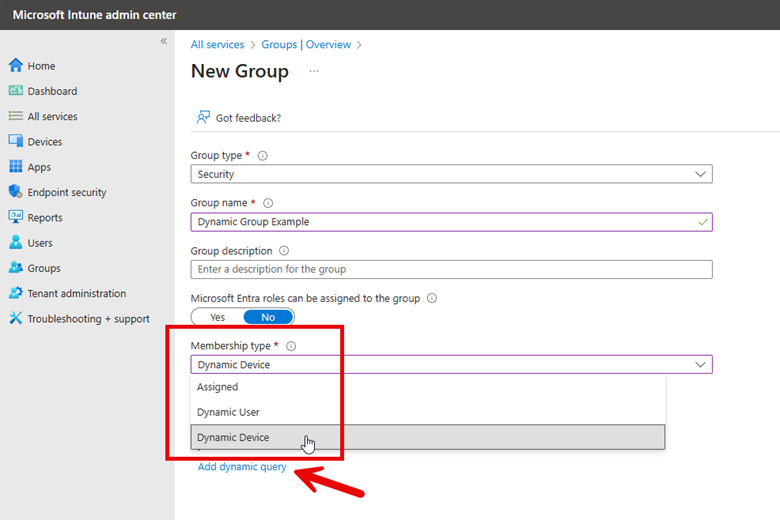
Now I need to create a dynamic query which will dictate the membership criteria. The screenshot above shows the “Add dynamic query” links that takes me to where I will create the Dynamic membership rules. Here you will use the wizard to create the rules that are comprised of properties, operators and values. You can add as many expressions as you want.
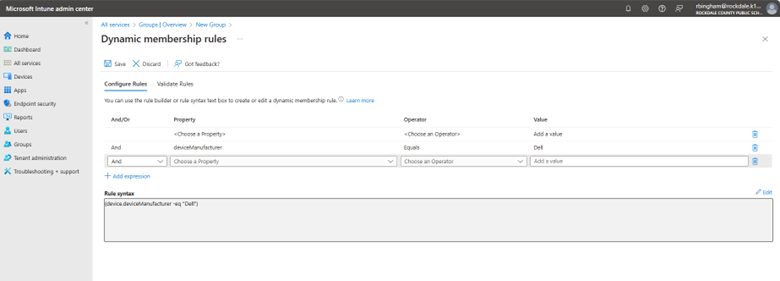
Here are some examples of possible groupings you can do:
- To automatically group all devices running Windows 11 the rule would be:
(device.operatingSystem -eq "Windows") and (device.deviceOSType -eq "11")
You can use this group to deploy security baselines policies or upgrade legacy systems.
- You can also make a group comprised of a specific Windows version such as Windows 11 24H2 Devices as follows:
(device.deviceOSVersion -startsWith "10.0.261") - Group All Users in a Specific Department such as Finance:
(user.department -eq "Finance")
- You can build composite rule sets combining multiple criteria, for example, a group that identifies corporate Windows 10 devices by validating both the operating system version and company ownership status in a single expression:
(device.deviceOSType -startsWith "Windows") and (device.deviceOSVersion -startsWith "10.0") and (device.deviceOwnership -eq "Company")
Dynamic Group Validation
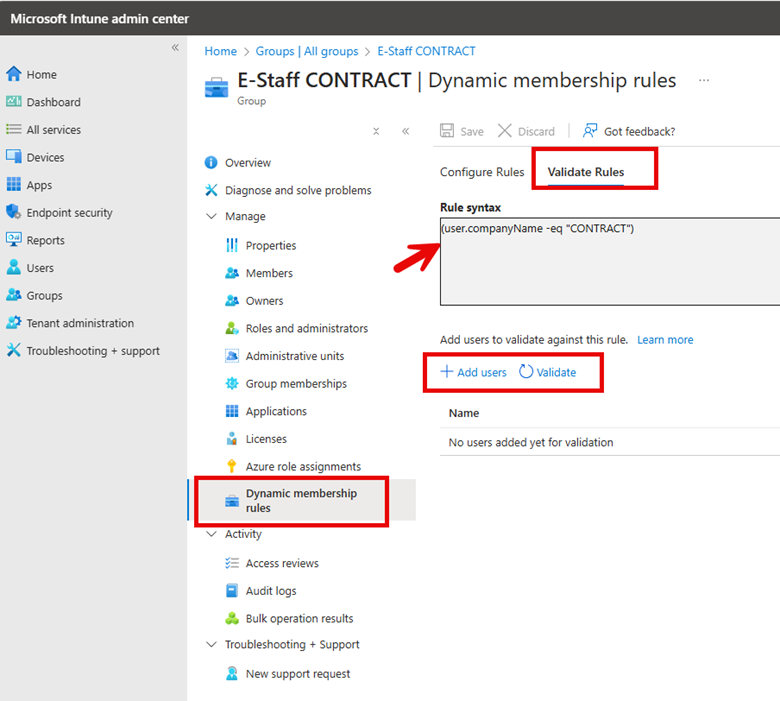
Before using new dynamic groups in a production environment, you should validate the rules to confirm that the dynamic rule results operate as expected. To do this, go to Groups in the Microsoft Intune admin center, select the group you want to validate, and navigate to the Dynamic membership rules section. Click "Validate Rules", add users or devices that should be included in the group, and then click "Validate" to confirm the proper assignment. The screenshot below outlines these steps.
Note that dynamic groups don't update instantly and may take up to 24 hours to process changes.
I mentioned there are two ways to create and validate Dynamic Groups because you can also use the Microsoft Entra ID portal using the exact steps I used in Intune. You can also use PowerShell to validate dynamic group membership using the following cmdlet:
$GroupID = "
$UserID = "
Get-MgGroupMember -GroupId $GroupID | Where-Object { $_.Id -eq $UserID }
If the output is empty, the user or device is not part of the group, meaning the rule might need adjustments.
As organizations continue to grow and evolve, the ability to automatically manage group memberships based on specific attributes becomes a necessity for maintaining security, compliance, and operational efficiency. By leveraging rule-based membership, these groups significantly reduce administrative overhead while ensuring that access controls, policy applications, and resource distributions remain current and accurate.