Why You Need to Checkout LAPS2 to Shore Up Security (Part 1)
Local Administrator Password Solution (LAPS) has been around for a while now. LAPS was released by Microsoft as a way for companies to avoid the practice of using a common password for all local administrator accounts. If a local administrator credential is compromised, a threat actor can then move laterally across your enterprise accessing one system after another using that single account.
LAPS acts as a type of password manager that issues a different password for a local administrator account on each designated device. That means if bad guys get a local password for one machine, they can’t get into another, so the breach is contained. Like a password manager, you don’t have to know the unique password for every local admin account because LAPS gives you a way to securely retrieve the password.
It would be nice if we didn’t need local administrator accounts at all, but unfortunately you can’t do everything through Group Policy, SCCM or an MDM. There is always going to be a task that calls for a support admin to log on to the machine to manually tweak something as an Admin... and that is where LAPS comes in. The original LAPS was a bolt on solution. You had to download the MSI from Microsoft and install it. The original release had a few shortcomings. The passwords could only be stored in Active Directory so those with Azure were out of luck. It also stored the password in plain text which leaves them potentially exposed.
The New LAPS
Microsoft just released the new version of LAPS in April 2023. It is designed to replace the original version which means we need a way to distinguish them both. Some refer to the original LAPS as “Legacy LAPS” but I prefer LAPS1. I will refer to the newest release as LAPS2 although Microsoft had named it Windows LAPS. One big differentiator is the fact that it also supports Azure Active Directory although it is currently only available in private preview. Since it isn’t universally available yet, we will focus on the new capabilities it brings to Windows Server Active Directory.
How to Get LAPS2
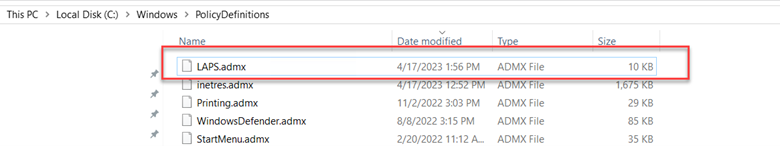
One difference right out of the gate is the fact that LAPS2 is natively integrated into Windows with KB5025229, OS Build 17763.4252 that was released on April 11, 2023. There’s nothing to manually download or install. Once the update is completed you need to retrieve the LAPS ADMX template file which will be located in Windows > PolicyDefinitions as shown in the screenshot below. Then just copy and paste the file in your central store. You will also need to copy the ADML file from your language folder, in my case, en-us.
I want to take a second to comment on a common misconception out there that Microsoft has abandoned on-prem AD and is focusing solely on the cloud. The release of LAPS2 demonstrates their continued commitment to investing in AD technology. There are thousands of enterprises out there that continue to use AD and LAPS2 helps to fill a critical security gap.
Implementing LAPS2 with Group Policy
KB5025299 adds a new Group Policy Object and AD schema attributes. If you are familiar with the LAPS1 then you were accustomed to navigating to Computer Configuration > Administrative Templates > LAPS where you had four settings to configure.
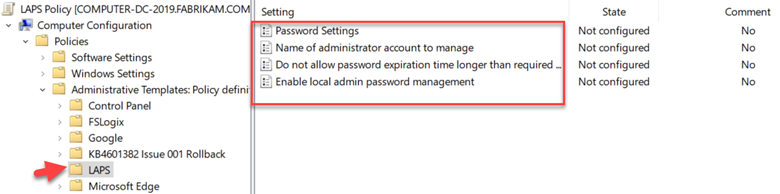
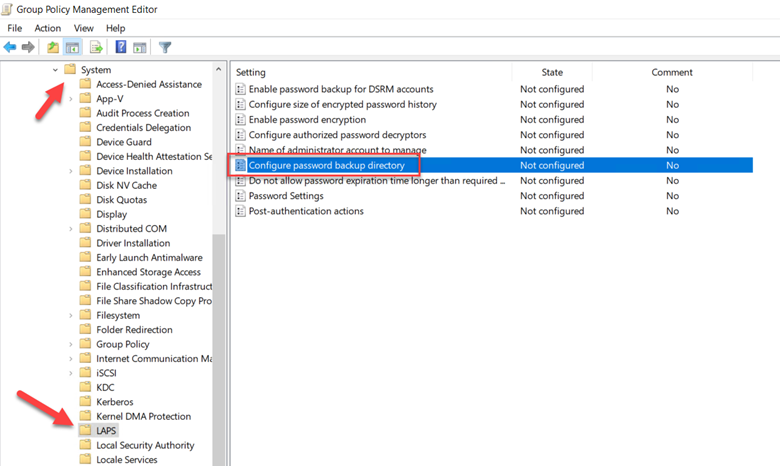
Well forget that path because LAPS2 settings are accessed by going to Computer Configuration > Administrative Templates > System > LAPS where we have more settings to choose from as shown below. To enable LAPS2 you must enable “Configure password backup policy.
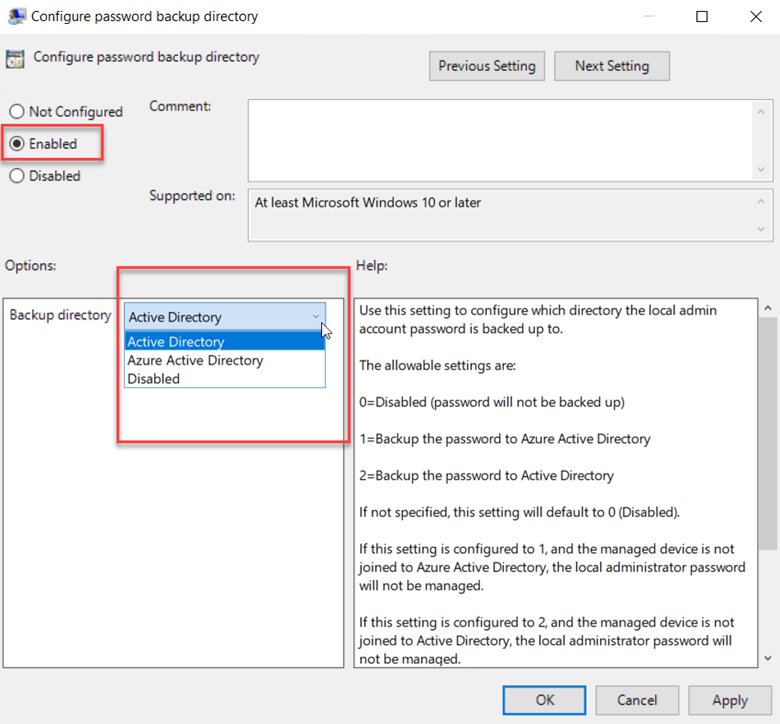
It’s in this setting that you will choose your backup directory. In this case I chose Active Directory below.
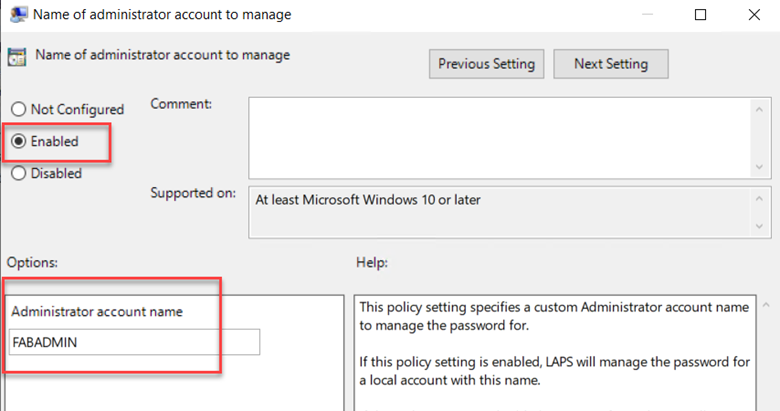
The next step should be to specify the name of the local admin account that will be assigned the passwords as shown in the example below.
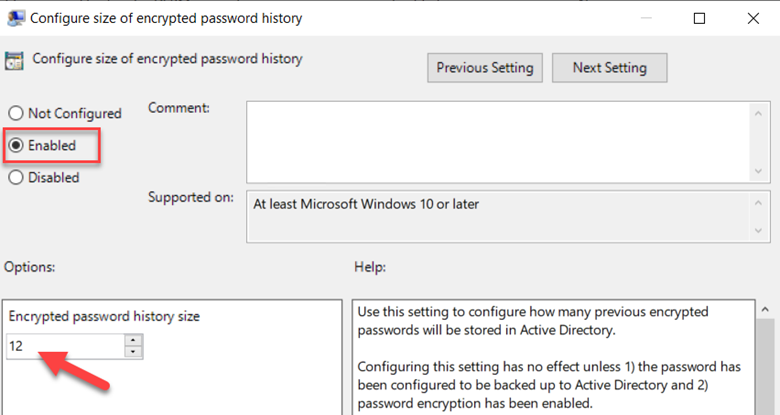
One new feature of LAPS2 is a configurable password history. This comes in handy if you need to restore a machine to a previous state in which the password was rotated. Group Policy lets you enable this feature and specify the size of your desired history (the maximum is 12) which I did below.
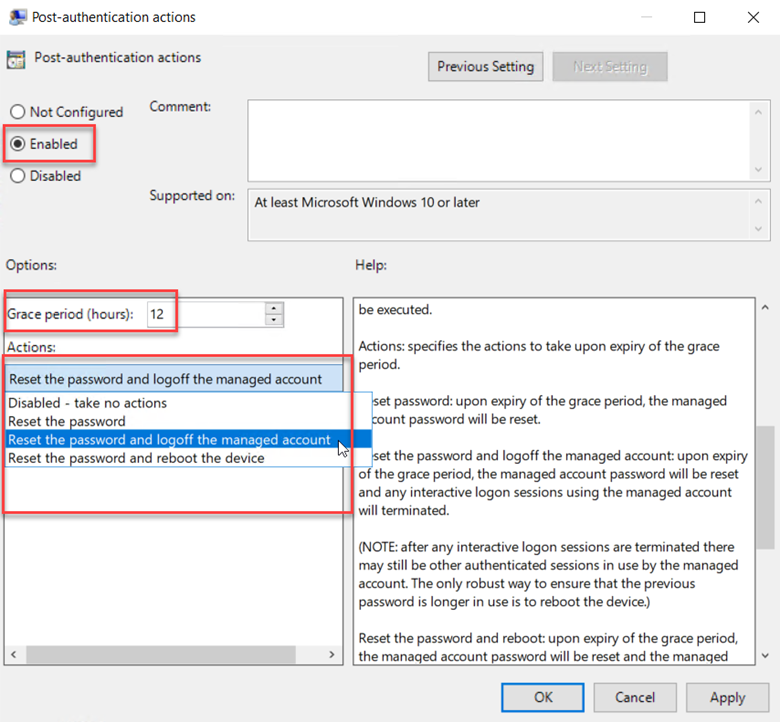
As mentioned, LAPS2 offers encryption to secure the passwords. This requires that you turn on the “Enable password encryption” setting. Another new feature is the ability to manage passwords for the Directory Service Restore Mode (DSRM) accounts. The “Enable password backup for DSRM accounts” setting has no effect unless the managed device is a domain controller and you have password encryption enabled. You can also configure “Post-authentication settings” to ensure that a password isn’t changed while a user is logged on by enforcing a delay or grace period after any successful login of a LAPS-managed account. When enabled, the policy allows you to state how long a grace period you want and select the designated action you want. In the example below I chose “Reset the password and logoff the managed account.”
In Part 2 of this discussion, we will look at the new PowerShell scripts that LAPS2 offers, the new LAPS property page in AD Users & Computers as well as how to operate LAPS and LAPS2 together.




Comments (0)