What are Azure Security Defaults and Who Should Use Them? (Part 1)
The old adage, “You can lead a horse to water but you can’t make them drink,” certainly applies to cybersecurity today. You can provide users and organizations with all types of cybersecurity tools and policies, but as long as they are optional, you cannot make them utilize them. A case in point is the enforcement of multifactor authentication (MFA) for Azure. Despite the fact that Microsoft attests that MFA will prevent 99.9 percent of account compromises, only around 8 percent of administrative accounts in Azure AD use it. In a world in which credential stuffing attacks initiate billions of malicious login attempts on a monthly basis, MFA should be an enforced policy for every organization. The hard truth is that we live in a digital world in which security is no longer optional.
Depreciation of Baseline Security Policies
Microsoft has already been providing a set of predefined policies to help organizations protect themselves against common attacks. There were four baseline policies.
- Require MFA for admins (preview)
- End user protection (preview)
- Block legacy authentication (preview)
- Require MFA for service management (preview
Azure admins could enable or disable them for their Azure userbase. Unfortunately, too many organizations have not taken advantage of these policies or the rich set of security capabilities such as Conditional Access. This not only makes them more vulnerable, but adds to the collective threat environment for everyone else as well. Every computer that is compromised serves as one more potential attack vehicle that perpetrators can use for malicious deeds towards others. The IT industry is starting to recognize that organizations not only have a responsibility to protect their own users, but share in the universal collective effort to make the world a less vulnerable place. By hardening up our own attack surfaces, we harden the world as well. As a result, Microsoft is depreciating these predefined policies on February 29, 2020, replacing them with the new “Security Defaults.”
What are Azure Security Defaults?
The intention of Security Defaults is simple; provide an enforced default security state for all Azure organizations that do not implement security policy initiatives on their own. Security Defaults are available to all tenants and like Baseline Security policies, are offered at no additional cost. New tenants will automatically have security defaults enabled by default. If your tenant was created on or after October 22, 2019, chances are that security defaults is already enabled. In the coming phase, Microsoft will begin retroactively enabling it for existing domains who have failed to enact any security measures on their own. These security defaults enforce the following:
- Unified Multi-Factor Authentication registration
- Multi-Factor Authentication enforcement
- Blocking legacy authentication
- Protecting privileged actions
If you are an existing tenant prior to the October date and currently and currently do not utilize security policies of any kind, you will need to enable Security Defaults for now. You can do this by going to Azure Active Directory > Properties > “Manage Security defaults” and set the Enable security defaults toggle to Yes as is shown below.
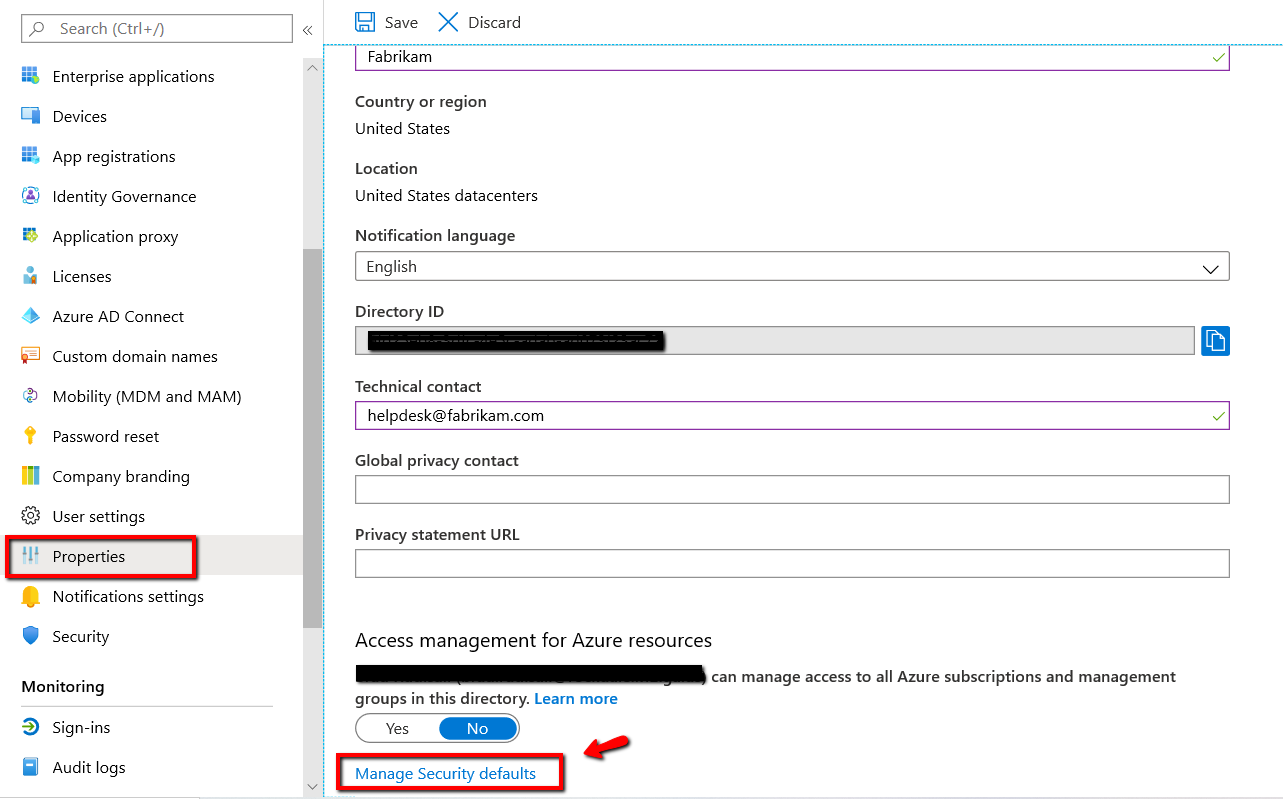
If you currently utilize Conditional Access, Classic or Identity Protection policies that consist of settings that may conflict with any of the security default offerings, you will receive an error message when trying to enable default security policies as is shown below.
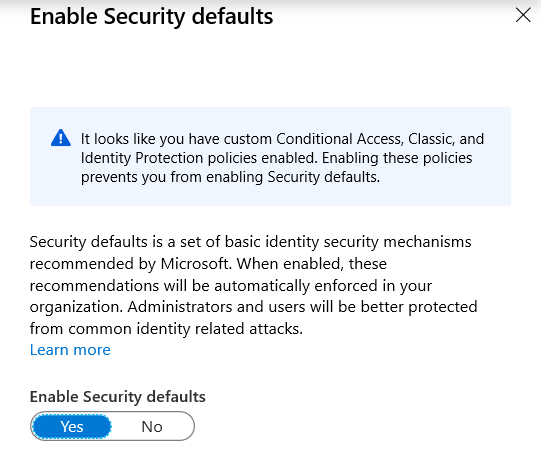
Note that you will have to disable Security defaults before creating conditional access or other security policies that involve conflicting settings. Keep in mind too that Security defaults is a bare minimum. While they may be appropriate for small organizations, medium or large enterprises should expand into policies that are more comprehensive.
MFA Registration
Let’s start with multifactor authentication. Security defaults require all users within the tenant to register for MFA. MFA requires a user to use a second method of authentication to prove their identity in addition to their logon credentials. The most popular method currently is SMS MFA in which the user must type in a unique one-time code sent to their cell phone after logging on with their assigned credentials. While this and other methods are available in Azure Conditional Access policies, it is not an available option under Security defaults. Azure Security defaults only utilizes the Microsoft Authenticator app
Once you enable Security defaults, users are required to register for MFA within 14 days. The 14-day clock starts from the time the user logs on for the first time once the security defaults are enabled. Should a user fail to register within this required time frame, the user will not be able to logon until the FMA registration is completed. The screenshot below shows what users will see during the 14-day registration period.
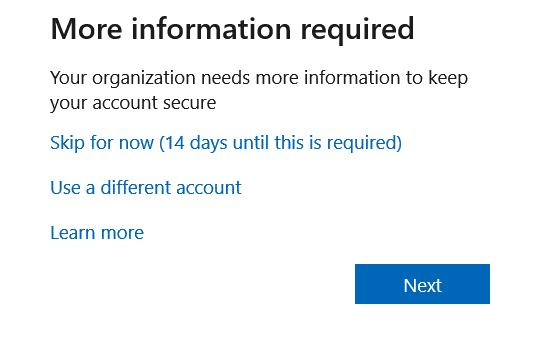
In addition to completing the MFA registration process, users must also install the Microsoft Authenticator app on their cell phone. We will cover Multi-Factor Authentication enforcement in Part 2 of this blog series.




Comments (0)