How to Enable Personal Data Encryption Using Intune
Personal Data Encryption (PDE) is a security feature introduced in Windows 11, version 22H2 that provides an additional encryption capability to Windows. PDE is different than BitLocker in that it encrypts individual files while BitLocker encrypts entire volumes. PDE utilizes Windows Hello for Business to link encryption keys with user credentials. This means you need only log on a single time while BitLocker requires a separate PIN be inputted. Another difference is that unlike BitLocker that releases data encryption keys at bootup, PDE releases them once a user signs in using Windows Hello for Business. Until then, users cannot access the protected file content.
There are 3 prerequisites for PDE:
- The computer must be Azure AD joined
- It must be running the Enterprise or Education edition of Windows 11, version 22H2 or later
- Windows Hello for Business Overview
Windows Hello provides fully integrated biometric authentication based on either facial recognition or fingerprint matching. Many laptops today have fingerprint readers or integrated compatible cameras to support it.
You should consider PDE as just another encryption layer for Windows on top of BitLocker that administrators can use to safeguard sensitive data. Don’t be confused by its name because standard users cannot initiate PDE, nor can they protect personal files with it. When you stop to think about it, it makes sense as you wouldn’t want malicious insiders to use it to hide data they shouldn’t have on their corporate devices. PDE can only be implemented by administrators who also selectively choose which filles to encrypt. PDE is ideal for business applications that work with sensitive files and should be heavily considered by those organizations that must adhere to compliance requirements.
You can enable PDE through Intune. By default, PDE on Windows 11 Devices in the Intune settings catalog is disabled. There are two ways to enable PDE in the Microsoft Intune Admin Center. The easiest way is to navigate to Devices > Configuration profiles and choose the Settings catalog as the profile. Using the Settings picker, search for personal data encryption and select the PDE category. Then check enable “Personal Data Encryption” as shown below.
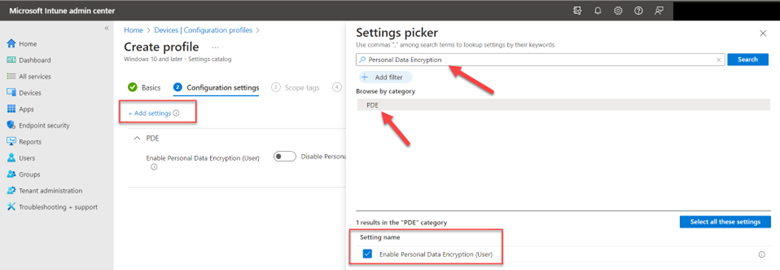
Assign the policy to the designated groups or users and save it. You can also use OMA-URI settings to create the policy using:
./User/Vendor/MSFT/PDE/EnablePersonalDataEncryption
as the OMA-URI path. Then choose integer as the data type with an assigned value as 1. The final configuration should look like the screenshot below.
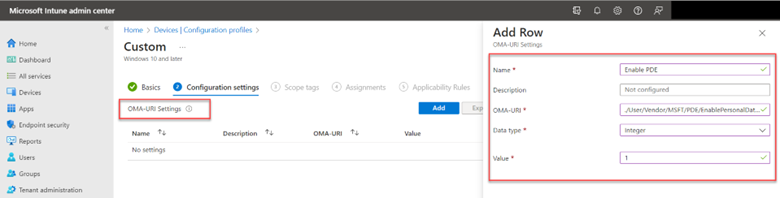
While support for PDE is limited currently, more applications will utilize it in the future.




Comments (0)