Everything you Want to Know about Managing Windows Updates (Part 4)
In our final segment of this series, we are going to wrap up our discussion concerning Windows update management. So now that you’ve configured your update rings and settings, you can create a compliance policy to reinforce them using Microsoft Endpoint Manager and going to the
“Devices |Overview” section and selecting Compliance policies near the bottom of the menu as shown below. Here you can also click on Compliance status and view the compliance status of your enterprise fleet
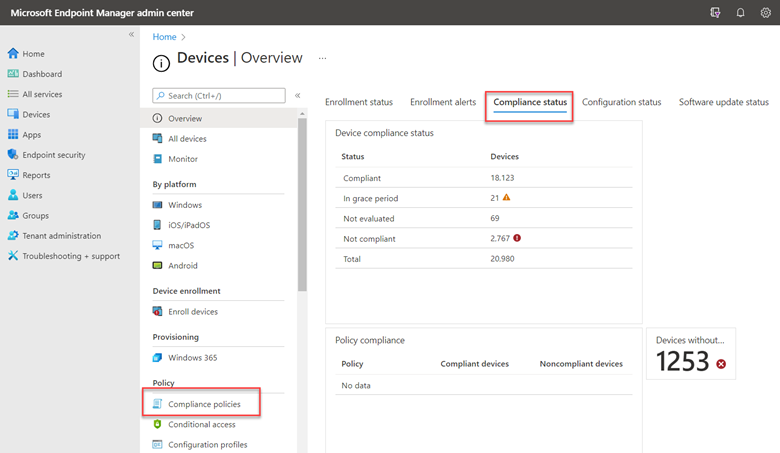
Create a new policy and choose Windows 10 and later as the platform. Name your policy and then go to Compliance settings > Device Properties. Here you can set the minimum OS version to be compliant. You can also set a maximum if desired. In the example below I have assigned 21H1 as the minimum OS version with 21H2 as the max.
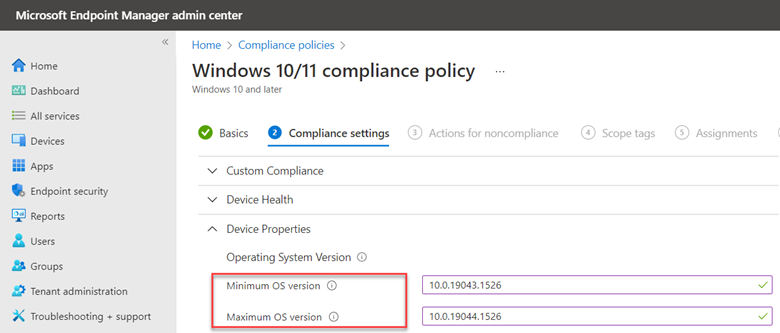
You can then determine what your action will be for non-compliant status. You can choose to either send an email to the user of the device or choose the hard-core action of retiring the device for noncompliance as shown in the screenshot below. A grace period of 3 days has also been configured.
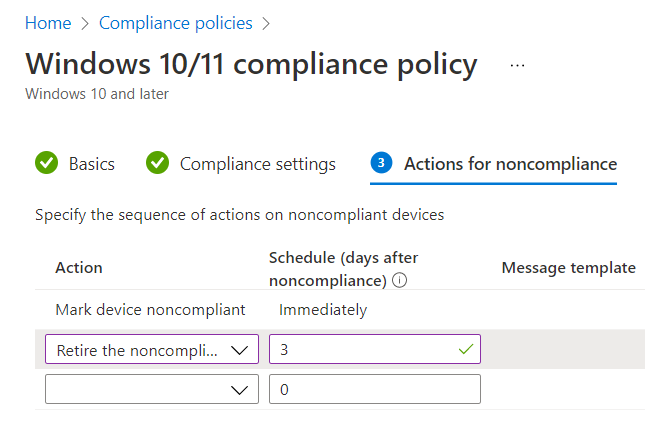
The final step is to assign the compliancy policy to your designated group(s).
Managing Updates in a Co-managed Environment
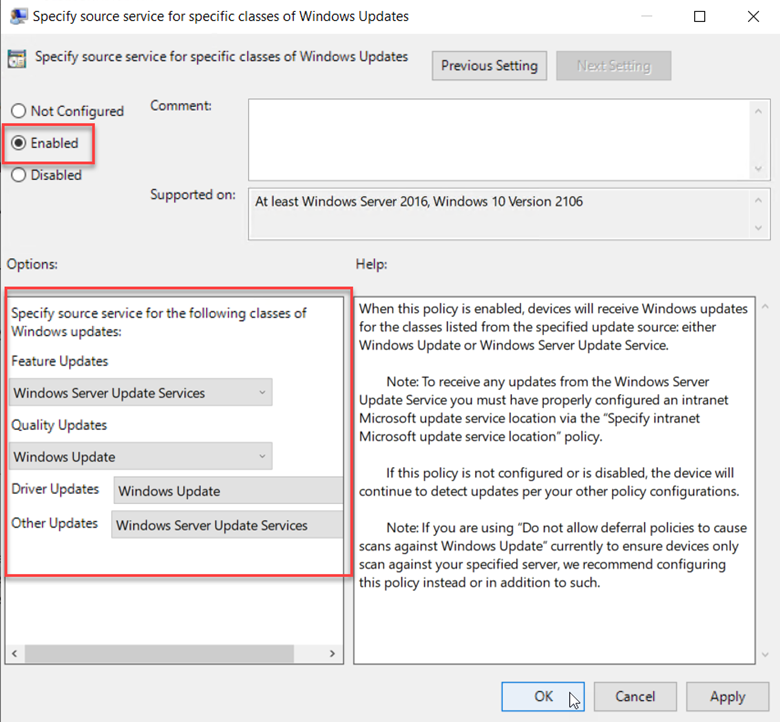
Those enterprises that use Microsoft Endpoint Manager Configuration Manager can utilize either WSUS or Windows Update as their update source. Here’s a good example of the flexibility this offers. Let’s create a GPO and go to Computer Configuration > Administrative Templates > Windows Components > Windows Update > Manage updates offered from Windows Server Update Service. Here you would configure settings to specify the IP address of the WSUS server. The settings we want to focus on is “Specify source service for specific classes of Windows Updates” as is shown in the screenshot below.
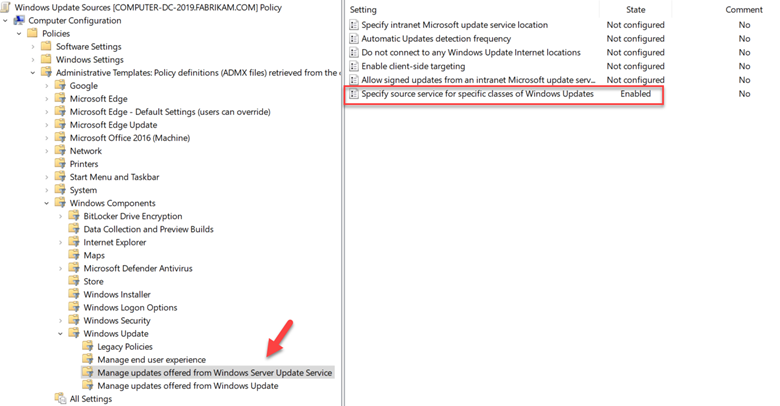
Enable the policy and then choose the source service for each update class. In the example below I am assigning the WSUS server as the feature update source and Windows Update for quality updates.
While we are in Group Policy, let’s look at some other useful settings. If you are fully managing the update environment for your end user devices, there is no need to perpetually send Windows update notifications to users. In the screenshot below I enabled the Display options for update notifications. Note that I have also enabled “Speficy deadlines to use Windows Updates and restarts” where just as I demonstrated in MEM earlier, you can assign a deferral period and grace period for Quality updates and Feature updates. I also chose to remove access to all Windows update features for good measure by enabling that policy.
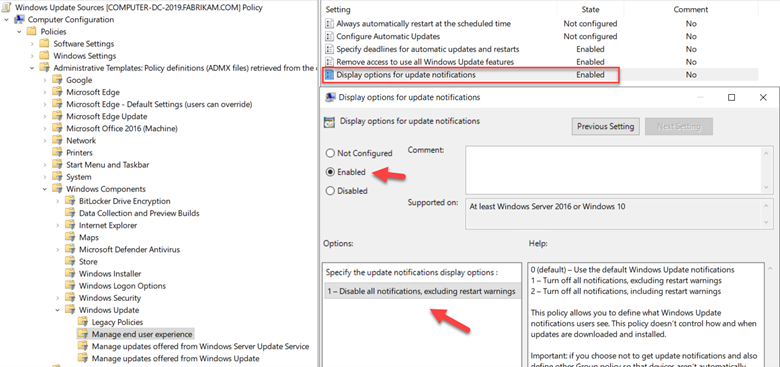
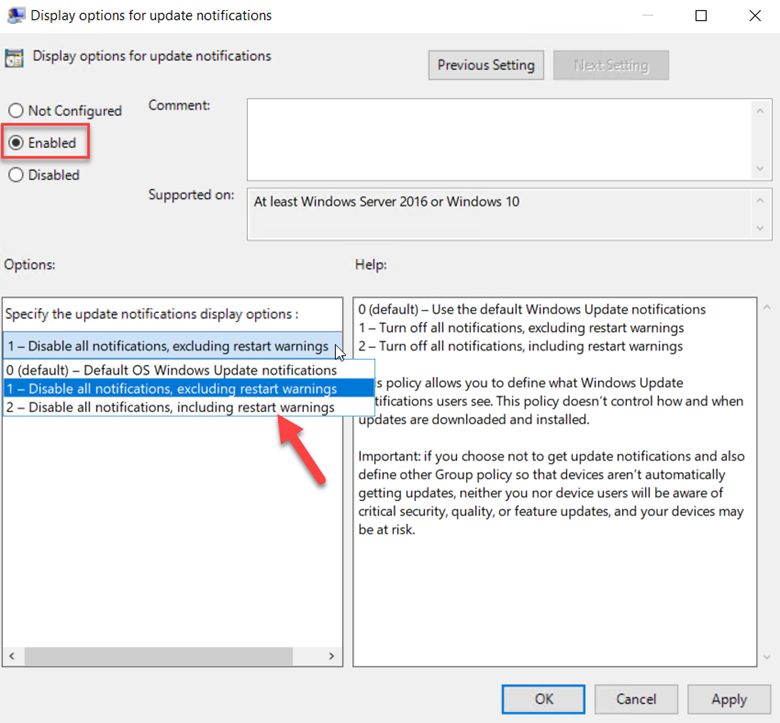
Here I chose to disable all update notifications other than restart warnings in order to give them a heads up about pending restarts.
Conclusion
Ensuring that all your Windows machines receive the latest quality updates is one of the most important steps you can do to secure your devices. Quality updates fix bugs and improve the reliability of your machines so that they run optimally for users. While feature updates are not as imperative, they cannot be ignored either as you need to make sure that users have access to new features that can help stimulate innovation and improve productivity. It’s a big job, but Microsoft provides the management tools to ensure that your machines remain update accordingly.




Comments (0)