Managing Removable Disks and Devices Using Group Policy and MEM
Your organization can invest in an entire portfolio of cybersecurity tools including email and web filtering, next generation firewall appliances and endpoint security solutions to protect your Windows computing devices. But deploying all those tools can still leave your machines vulnerable to zero-day attacks and malware infestations. That’s because all the filtering and firewall policies in the world won’t stop malicious code from being transferred from an insertable USB stick. The USB port remains a viable attack avenue for hackers and their malicious code creations to infiltrate computers thanks to users sharing USB drives. Fortunately, there are easy ways to manage removable storage access for your fleet of enterprise Windows devices.
Using Group Policy
Let’s start with Group Policy. You can manage removable storage settings on the Computer or User side. A Computer policy would prevent IT personnel with admin privileges from using USB sticks, thus preventing them from performing some of their everyday tasks. The purpose of this policy is to prevent standard users from transferring malicious code, so a User Configuration policy makes the most sense. Create a GPO and go to User Configuration > Administrative Templates > System > Removable Storage Access as shown below.
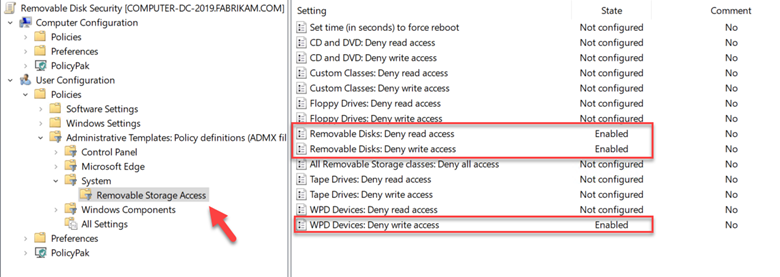
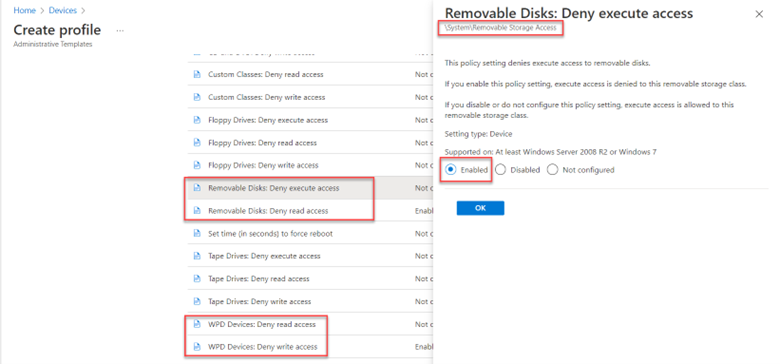
Let’s clear up any confusion concerning the various removable storage options listed. If you are younger than age 30 you probably don’t know what a floppy disk is and that’s a good thing. For most modern computers today, you need only worry about Removable Disks (USB sticks and external drives) and Windows Portable Devices which include things such as smart phones, cameras, etc. An example would be transferring pictures from a smart phone to a laptop. In the screenshot above I have enabled settings to deny read and write access to removable disks and denied write access to WPD devices.
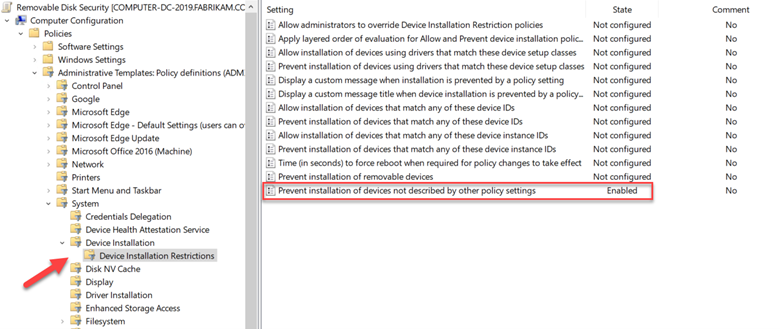
Another option is to prevent users from installing removable devices onto their machines. You can only do this on the Computer side but there is a setting called “Prevent installation of devices not described by other policy settings” that is perfect for this situation. You can find it by going to Computer Configuration > Administrative Templates > System > Device Installation Restrictions. The enabled policy is shown below.
Using MEM
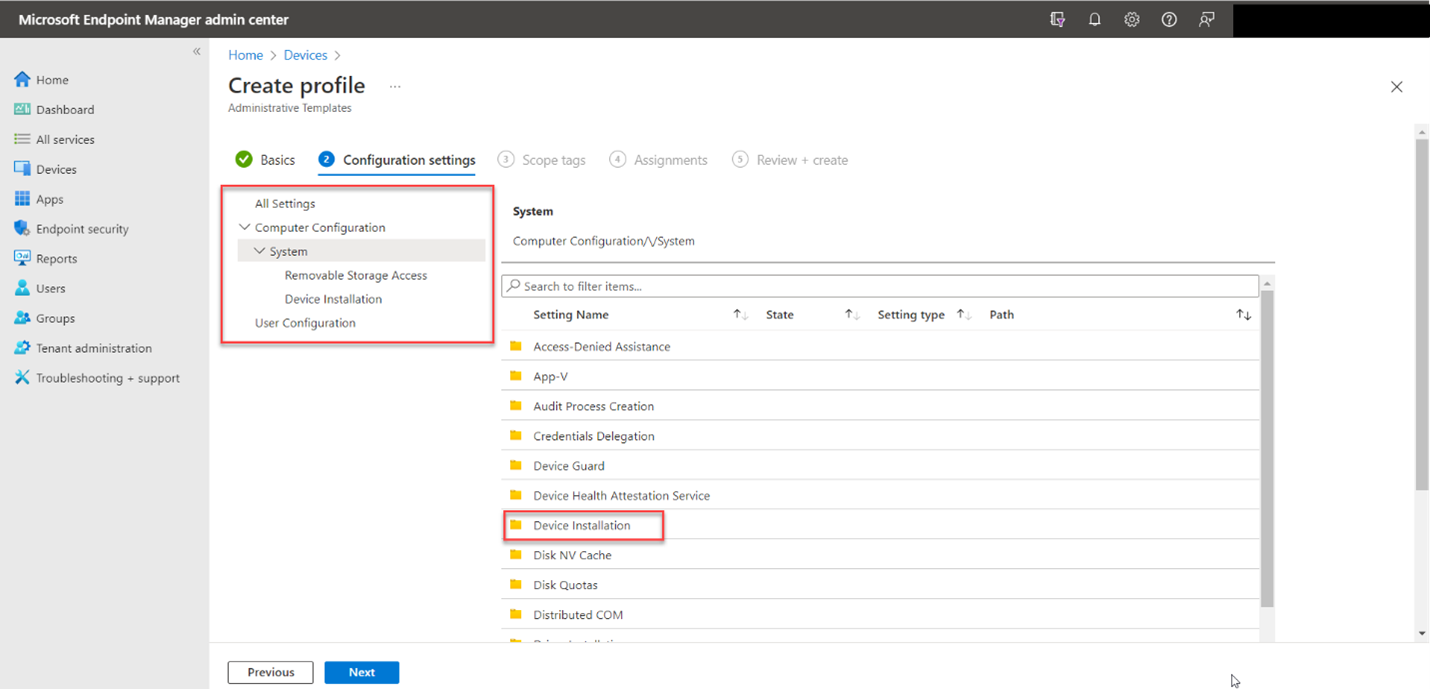
You can also configure removable storage policies using Microsoft Endpoint Manager. There are a couple of ways to do it. The first is to go to Devices > Configuration profiles and create a profile. Select “Windows 10 and later” as the platform and Templates as the Profile > then choose Administrative Templates from the list of available templates. Name the policy and then drill down to System. Here you will find both groups of desired settings as shown below.
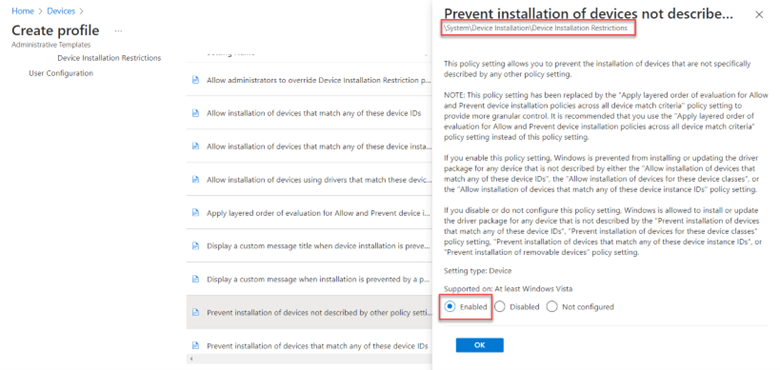
Drilling down into Device Installation we can enable the “Prevent installation of devices not described by other policy settings” policy for MDM enrolled devices.
You can then go up one level and scroll over to the Removable Storage Access settings. Below I have enabled the “Removable Disks: Deny execute access” setting.
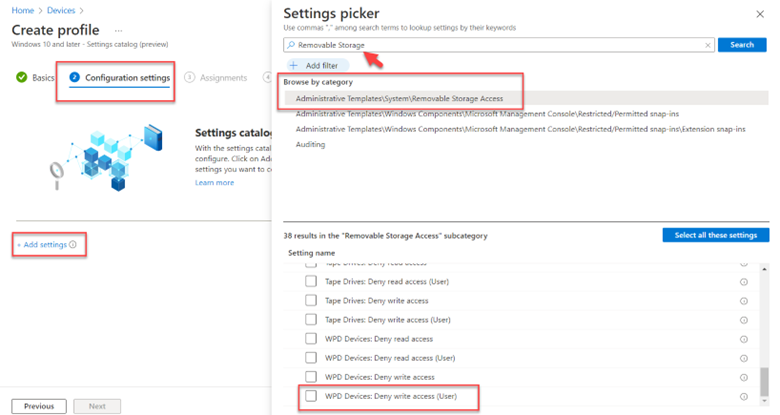
You can also configure these settings using the Settings picker. Rather than choosing Templates as the profile type, select Settings. Then use the Settings picker to search for “Removable Storage” and select the correct category. Then choose the desired settings in the section below and configure them as shown in the screenshot below. You can do the same then for Device Installation settings.




Comments (0)